Born to be cloud
Creating robust digital systems that flourish in an evolving landscape. Our services, spanning from Cloud to Applications, Data, and AI, are trusted by 150+ customers. Collaborating with our global partners, we transform possibilities into tangible outcomes.

.png)
.png)












.png)













.png)






.png)
.png)












.png)













.png)






.png)
.png)












.png)













.png)






.png)
.png)












.png)













.png)





Experience our services.
We can help to make the move - design, built and migrate to the cloud.
Cloud Migration
Maximise your investment in the cloud and achieve cost-effectiveness, on-demand scalability, unlimited computing, and enhanced security.
Artificial Intelligence/ Machine Learning
Infuse AI & ML into your business to solve complex problems, drive top-line growth, and innovate mission critical applications.
Data & Analytics
Discover the Hidden Gems in Your Data with cloud-native Analytics. Our comprehensive solutions cover data processing, analysis, and visualization.
Generative Artificial Intelligence (GenAI)
Drive measurable business success with GenAI, Where creative solutions lead to tangible outcomes, including improved operational efficiency, enhanced customer satisfactions, and accelerated time-to-market.
.png)
.png)
Ankercloud: Partners with AWS, GCP, and Azure
We excel through partnerships with industry giants like AWS, GCP, and Azure, offering innovative solutions backed by leading cloud technologies.



Our Specializations & Expertise
.svg)
-p-500.png)
Countless Happy Clients and Counting!
.png)
.png)
Check out our blog

The Future of Autonomous Workflows: Agentic AI by Ankercloud
The Automation Paradox: Why Traditional ML is Hitting a Wall
Enterprises today are caught in a paradox: they need to innovate faster than ever, yet their core machine learning models require manual intervention, resulting in delays, inconsistent outcomes, and scalability challenges. Traditional AI is powerful, but it often requires fragmented processes and constant "babysitting", someone to manually shepherd data preparation, deployment, and monitoring. This operational friction turns promising AI projects into bottlenecks.
This is why Agentic AI represents a strategic necessity. It is the evolution from reactive data modeling to proactive, goal-driven automation. Agentic AI shifts the paradigm by acting autonomously, orchestrating complex workflows end-to-end to deliver results without constant human oversight. This allows businesses to accelerate innovation and unlock new sources of value that were previously unattainable.
Agentic AI: The New Paradigm of Goal-Driven Autonomy
Agentic AI is a new class of intelligent systems designed not just to process data, but to take initiative and complete high-level objectives. The key differentiator is autonomy:
- Autonomy in Action: Agentic AI can orchestrate the entire ML lifecycle, from identifying and preparing data to training models, deploying them, and ensuring continuous monitoring, making ML projects truly end-to-end and repeatable.
- Faster Delivery with Consistency: This automation allows our customers to scale their AI initiatives without the usual bottlenecks, achieving accelerated time-to-value and continuous enhancement with superior reliability.
This shift means your organization is no longer deploying static code; you are deploying intelligent systems that learn, adapt, and drive business goals forward.
The Collaborative Future: Agents, Protocols, and Speed
The true power of Agentic AI is its ability to break down silos and enable fluid collaboration, not just between humans and AI, but between multiple AI agents themselves.
- Seamless Connectivity: Agentic AI incorporates data and APIs from disparate sources, regardless of their location or format, into cohesive, orchestrated workflows.
- The Collaboration Layer: Ankercloud leverages emerging technologies like Model Context Protocol (MCP) and Agent to Agent Protocol (A2A) frameworks. These protocols enable multiple agents and sub-agents to collaborate much like a real-world problem-solving team, delivering smarter, fully automated workflows that address complex industry challenges with precision.
This connectivity enhances integration across all your enterprise systems, allowing us to deliver offerings previously out of reach, such as intelligent chatbots, complex data processing pipelines, and dynamic content generation tailored to customer needs.
Ankercloud: Your Architect for the Autonomous Enterprise
Transitioning to autonomous workflows requires more than just access to powerful models; it demands specialized expertise in cloud architecture, security, and continuous governance.
- Secure Cloud Expertise: As a premier partner of Google Cloud Platform (GCP) and AWS, Ankercloud brings unparalleled expertise. We integrate secure, reliable cloud-native managed services like Google Vertex AI Agents and AWS Bedrock Agents into our solutions. This approach guarantees high accuracy, robust performance, and regulatory compliance while minimizing operational overhead for our clients.
- Methodology and Trust: Agentic AI is a strategic enabler that drives substantial, measurable business outcomes. Paired with Ankercloud’s deep cloud security insights and mastery of the full ML lifecycle, customers gain confidence in adopting autonomous workflows that transform efficiency, boost quality, and increase agility across their operations.
Conclusion: The Future of Work is Autonomous
The competitive landscape of the future belongs to enterprises that can successfully implement goal-driven automation. Agentic AI is not just about technology; it’s about a new strategic methodology that frees your organization from manual, repetitive tasks, allowing your human talent to focus on innovation and high-value strategic initiatives.
Are you ready to unlock the potential of Agentic AI?
Partner with Ankercloud to begin your journey toward the autonomous future, where AI works smarter, faster, and safer for your enterprise.
2

Cyber threats aren’t slowing down, why should your defenses?
Cloud adoption has outpaced traditional security postures. With exposed APIs, hybrid workloads, and multi-cloud architectures, the cloud attack surface has expanded exponentially. Recent events such as the 2025 16-billion credential leak and global ransomware campaigns highlight one uncomfortable truth: Identity and Access Management (IAM) weaknesses remain the leading cause of breaches.
The misconfigurations are well known, stale credentials, over-privileged IAM roles, insufficient multi-factor authentication (MFA), and unmanaged API tokens—but eliminating them at enterprise scale requires more than manual policy enforcement.
This is where Ankercloud’s achievement of the AWS Security Competency makes the difference. Backed by AWS’s rigorous validation, we provide enterprises with a proven, automated approach to securing identities, access, and workloads across complex environments.
Technical Pillars of Ankercloud’s AWS Security Competency
1. Automated Identity & Access Controls (CIEM + PAM)
- Continuous identity auditing powered by Cloud Infrastructure Entitlements Management (CIEM).
- Enforces least privilege by removing stale IAM users, deactivating unused access keys, and tightening role-based permissions.
- Integrated Privileged Access Management (PAM) to control, monitor, and rotate high-privilege credentials.
- Automated guardrails detect and remediate token sprawl, stopping unauthorized lateral movement.
2. Zero Trust and Continuous Verification
- Enforces Zero Trust Architecture across APIs, containers, and serverless functions.
- Real-time, context-aware access validation based on user identity, device posture, location, and workload sensitivity.
- Prevents privilege escalation, ransomware propagation, and insider threats through just-in-time (JIT) authorization.
3. AI-Powered Runtime Threat Detection
- Multi-source telemetry from AWS GuardDuty, AWS Security Hub, CloudTrail, and endpoint agents.
- Machine learning–driven anomaly detection and behavioural analytics to identify zero-day exploits, command-and-control traffic, and unusual API calls.
- Runtime security integration across Kubernetes, ECS, and Lambda functions to stop threats in real-time.
4. Compliance Automation for Regulatory Readiness
- Automated control mapping to GDPR, HIPAA, ISO 27001, and EU data protection standards.
- Continuous compliance monitoring and audit log ingestion into governance workflows.
- On-demand compliance reporting reduces manual audit overhead while ensuring continuous enforcement.
5. Unified & Scalable Security Operations (Cloud-Native SOC)
- Centralized telemetry ingestion across infrastructure-as-code, CI/CD pipelines, workloads, and SOC dashboards.
- Automated incident prioritization and response powered by AI-driven correlation.
- Mean-Time-To-Remediate (MTTR) reduced from weeks to minutes through playbook-driven workflows.
- 24/7 Managed Detection and Response (MDR) to scale protection across enterprise cloud environments.
Real-World Impact Across Industries
- Financial Services: Detected and prevented unauthorized IAM privilege escalation attempts, eliminating high-risk lateral movement paths across AWS and Azure environments.
- Healthcare: Automated HIPAA and GDPR compliance reporting integrated into the SOC, reducing security alert fatigue by 50% and streamlining audit readiness.
Why Choose Ankercloud
With cloud complexity increasing, security leaders can no longer rely on reactive, manual IAM policies. Enterprises require automated, scalable, validated solutions that close IAM gaps while reducing operational overhead.
Ankercloud’s AWS Security Competency demonstrates our technical excellence in:
- Eliminating IAM misconfigurations
- Enforcing Zero Trust policies
- Detecting advanced threats at runtime
- Automating compliance frameworks
- Scaling Security operations for cloud-native environments
By partnering with Ankercloud, enterprises gain a resilient IAM foundation that protects data, meets regulatory standards, and accelerates secure innovation.
2

From RBAC Chaos to PBAC Control: Data Governance on AWS
What if your data lake became a security labyrinth instead of a data goldmine? For too long, managing access to sensitive data in the cloud has felt like an endless game of patching permissions and untangling a web of static roles. Traditional access models like Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC) were the guardians of yesterday, but they are no match for the dynamic, multi-tenant needs of today’s large-scale data environments. In a world where compliance frameworks like GDPR and HIPAA are non-negotiable and data serves as a strategic product, these rigid methods often lead to over-permissioning, security vulnerabilities, and operational headaches.
That’s where Purpose-Based Access Control (PBAC) emerges not just as a better option, but as a strategic evolution in data governance. PBAC shifts the focus from static permissions to dynamic, context-aware access decisions driven by the specific purpose of the request. Instead of simply asking “Who are you?” or “What attributes do you have?”, PBAC also asks “Why do you need this data right now?”.
By incorporating the intended purpose into the decision-making process, PBAC delivers unmatched flexibility, security and compliance ensuring users get only the data necessary for their declared and approved purpose. This approach transforms your data lake from a potential liability into a governed, high-value business asset.
At Ankercloud, we take a research driven approach to implementing PBAC in modern cloud environments, leveraging AWS-native tools and custom policy logic to create secure, purpose-driven access frameworks that scale with your business.
Why Traditional Access Models Fall Short
The core of the problem with older models lies in their rigidity. RBAC, for example, assigns permissions based on static roles. As data environments grow, this can lead to a "role explosion," with dozens or even hundreds of roles to manage, making audits and updates a nightmare. ABAC introduced more flexibility by using attributes, but it too can become complex and unwieldy, requiring constant updates to maintain relevance.
These models struggle to keep pace with the modern reality of:
- Fine-Grained Access: The need for granular control over shared datasets at the column or cell level.
- Compliance Pressures: Strict frameworks like GDPR and HIPAA demand access controls that are provable and dynamically enforceable.
- Data as a Product: The shift to treating data as a product requires scalable, secure, and self-service access to accelerate innovation without compromising security.
PBAC offers a powerful alternative by decoupling access decisions from users, roles, or static attributes. Instead, it evaluates access based on centralized, dynamic policies, allowing for more flexibility, granularity, and maintainability.
A Research-Driven Approach: Implementing PBAC on AWS
Our team at Ankercloud recently explored how Purpose Based Access Control can be implemented in a modern AWS environment using native services. The goal was to evaluate how scalable and secure PBAC can be in real world data architectures. This research driven approach centers around three core AWS components that work in concert to create a robust and dynamic access control system:
- AWS Lake Formation LF-Tags: These tags are a powerful mechanism to define fine-grained access rules directly on your data assets. By applying tags like region=EU or department=Finance to specific tables, databases, or columns, you can create logical groupings that form the basis of your access policies.
- AWS Lambda: This is the brains of the operation. AWS Lambda serves as the dynamic policy engine, evaluating a user's context (e.g., their identity, the time of day, their device) against the LF-Tags of the requested data to make a real-time authorization decision.
- Amazon API Gateway: Acting as the secure entry point, API Gateway routes all data access requests to the Lambda function. This ensures that no data can be accessed without first passing through your centralized policy enforcement point, guaranteeing a single, auditable path for all data queries.
This architecture creates a seamless, secure, and scalable flow: a request comes in, API Gateway sends it to Lambda, Lambda checks the policy against the data's tags, and access is granted or denied all in real-time.
Top Use Cases & Real-World Impact
The power of PBAC truly shines in complex, distributed data environments. Consider a global retail company with departments like Marketing, Finance, and Supply Chain all accessing a shared enterprise data lake. The challenge is ensuring each department has restricted access based on region, role, or data type while meeting strict compliance standards.
- The Traditional Problem: Implementing this with RBAC would require creating dozens of static IAM roles and manually managing views for each department, leading to a high risk of over-permissioned access and administrative overhead.
- The PBAC Solution: With PBAC on AWS, data is tagged using LF-Tags (e.g., department=Marketing, region=EU, data_type=PII). An API Gateway handles incoming requests, and Lambda enforces policies in real-time. For example, a Marketing analyst from the EU requests customer data. PBAC automatically checks their access against the LF-Tags, and if the policy matches, access is granted otherwise, it is denied all without any manual intervention.
This approach is also critical for:
- Healthcare:
Ensuring doctors, researchers, and administrators only have access to specific patient data based on their role, location, or data sensitivity (e.g., genetic data vs. demographic data), aligning perfectly with HIPAA. - Financial Services:
Implementing granular controls for financial data, allowing analysts to view market trends without accessing sensitive customer account details, thereby meeting strict regulatory requirements. - Insurance Domain:
Enforcing purpose-driven access so claims adjusters can view only active claim files relevant to their region, underwriters can access risk assessment data without seeing personal health details, and fraud investigators can analyze flagged cases—supporting compliance with industry regulations and protecting customer privacy.
Basic idea of Implementation of PBAC Workflow in AWS
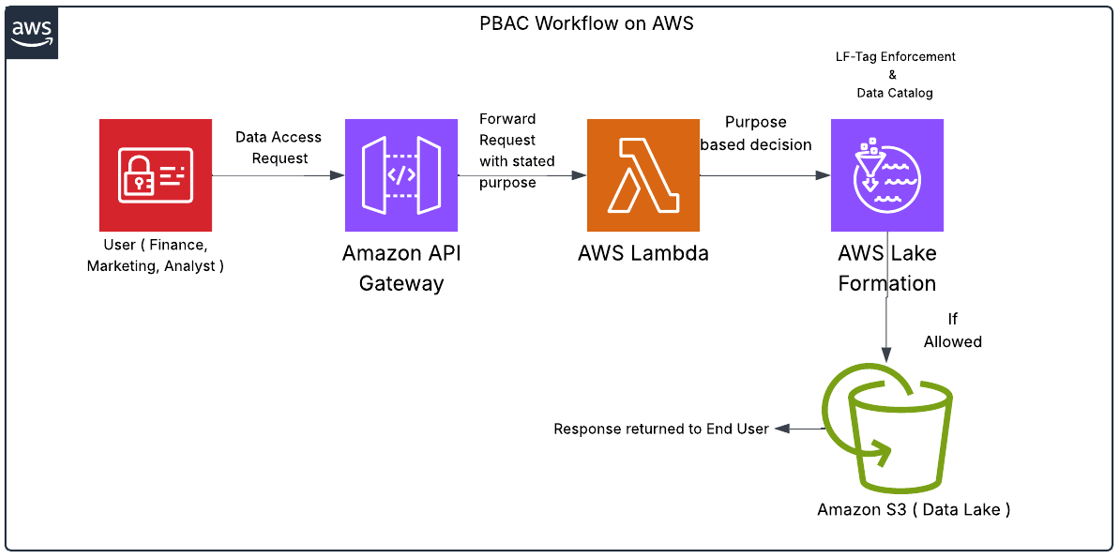
In AWS, Purpose Based Access Control (PBAC) uses dynamic, context-aware rules to decide who can access which data.
- User Request – A Marketing analyst, Finance officer, or Data analyst sends a query to the data lake through Amazon API Gateway.
- Purpose Evaluation – API Gateway forwards the request to an AWS Lambda purpose based engine, which checks:
- User context (identity, department, region, time, device)
- LF-Tags on the requested data (e.g., department=Finance, region=EU, data_type=PII) in AWS Lake Formation
- User context (identity, department, region, time, device)
- Decision – Lambda compares the user’s attributes to the LF-Tag policy:
- Match → Access granted
- No match → Access denied
- Match → Access granted
- Data Delivery – If approved, Lake Formation grants access to the dataset stored in Amazon S3 or queried via the Glue Data Catalog.
- Audit & Monitoring – Every decision is logged in CloudWatch and CloudTrail for compliance tracking (e.g., GDPR, HIPAA).
Example:
- A Marketing analyst in the EU requests customer purchase data. The Lambda engine checks that their department and region match the LF-Tags on the dataset. If tags match (department=Marketing, region=EU), they get access; if not, the request is denied—no manual intervention needed.
The Path to Modern Data Access: How Ankercloud Helps
Embracing PBAC is a strategic move, but its implementation requires deep expertise in modern cloud architecture, data governance, and security best practices. At Ankercloud, we don't just explore these solutions, we build them. We bring a proven, research-driven approach to help businesses transition from outdated access models to a dynamic and secure PBAC framework.
Our specialized services include:
- Strategic Consulting: We help you define your data governance and security objectives, translating them into a clear Purpose Based Access Control (PBAC) roadmap.
- Architecture & Implementation: We design and deploy the entire PBAC architecture on AWS, leveraging native services like Lake Formation, Lambda, and API Gateway for a scalable and secure solution.
- Custom Purpose Engine Development: We build and optimize your dynamic purpose evaluation engine, ensuring it's robust, efficient, and fully aligned with your business logic.
- Continuous Governance: We provide ongoing support to monitor, audit, and evolve your PBAC rules, ensuring your data remains secure and compliant as your business grows.
Our approach is rooted in continuous growth and learning. Big thanks to my team at Ankercloud for their dedication to exploring and building innovative solutions like this.
The future of business is autonomous, adaptive, and intelligent. Purpose Based Access Control ( PBAC) is the key to unlocking this potential securely. It is time to move beyond static, brittle access controls and empower your teams with safe, governed, and purpose-driven data access.
Ready to modernize your data access strategy?
Partner with Ankercloud to implement a cutting-edge PBAC solution that fortifies your data lake and accelerates your innovation. Contact us today.
2
The Future of Autonomous Workflows: Agentic AI by Ankercloud
The Automation Paradox: Why Traditional ML is Hitting a Wall
Enterprises today are caught in a paradox: they need to innovate faster than ever, yet their core machine learning models require manual intervention, resulting in delays, inconsistent outcomes, and scalability challenges. Traditional AI is powerful, but it often requires fragmented processes and constant "babysitting", someone to manually shepherd data preparation, deployment, and monitoring. This operational friction turns promising AI projects into bottlenecks.
This is why Agentic AI represents a strategic necessity. It is the evolution from reactive data modeling to proactive, goal-driven automation. Agentic AI shifts the paradigm by acting autonomously, orchestrating complex workflows end-to-end to deliver results without constant human oversight. This allows businesses to accelerate innovation and unlock new sources of value that were previously unattainable.
Agentic AI: The New Paradigm of Goal-Driven Autonomy
Agentic AI is a new class of intelligent systems designed not just to process data, but to take initiative and complete high-level objectives. The key differentiator is autonomy:
- Autonomy in Action: Agentic AI can orchestrate the entire ML lifecycle, from identifying and preparing data to training models, deploying them, and ensuring continuous monitoring, making ML projects truly end-to-end and repeatable.
- Faster Delivery with Consistency: This automation allows our customers to scale their AI initiatives without the usual bottlenecks, achieving accelerated time-to-value and continuous enhancement with superior reliability.
This shift means your organization is no longer deploying static code; you are deploying intelligent systems that learn, adapt, and drive business goals forward.
The Collaborative Future: Agents, Protocols, and Speed
The true power of Agentic AI is its ability to break down silos and enable fluid collaboration, not just between humans and AI, but between multiple AI agents themselves.
- Seamless Connectivity: Agentic AI incorporates data and APIs from disparate sources, regardless of their location or format, into cohesive, orchestrated workflows.
- The Collaboration Layer: Ankercloud leverages emerging technologies like Model Context Protocol (MCP) and Agent to Agent Protocol (A2A) frameworks. These protocols enable multiple agents and sub-agents to collaborate much like a real-world problem-solving team, delivering smarter, fully automated workflows that address complex industry challenges with precision.
This connectivity enhances integration across all your enterprise systems, allowing us to deliver offerings previously out of reach, such as intelligent chatbots, complex data processing pipelines, and dynamic content generation tailored to customer needs.
Ankercloud: Your Architect for the Autonomous Enterprise
Transitioning to autonomous workflows requires more than just access to powerful models; it demands specialized expertise in cloud architecture, security, and continuous governance.
- Secure Cloud Expertise: As a premier partner of Google Cloud Platform (GCP) and AWS, Ankercloud brings unparalleled expertise. We integrate secure, reliable cloud-native managed services like Google Vertex AI Agents and AWS Bedrock Agents into our solutions. This approach guarantees high accuracy, robust performance, and regulatory compliance while minimizing operational overhead for our clients.
- Methodology and Trust: Agentic AI is a strategic enabler that drives substantial, measurable business outcomes. Paired with Ankercloud’s deep cloud security insights and mastery of the full ML lifecycle, customers gain confidence in adopting autonomous workflows that transform efficiency, boost quality, and increase agility across their operations.
Conclusion: The Future of Work is Autonomous
The competitive landscape of the future belongs to enterprises that can successfully implement goal-driven automation. Agentic AI is not just about technology; it’s about a new strategic methodology that frees your organization from manual, repetitive tasks, allowing your human talent to focus on innovation and high-value strategic initiatives.
Are you ready to unlock the potential of Agentic AI?
Partner with Ankercloud to begin your journey toward the autonomous future, where AI works smarter, faster, and safer for your enterprise.
Cyber threats aren’t slowing down, why should your defenses?
Cloud adoption has outpaced traditional security postures. With exposed APIs, hybrid workloads, and multi-cloud architectures, the cloud attack surface has expanded exponentially. Recent events such as the 2025 16-billion credential leak and global ransomware campaigns highlight one uncomfortable truth: Identity and Access Management (IAM) weaknesses remain the leading cause of breaches.
The misconfigurations are well known, stale credentials, over-privileged IAM roles, insufficient multi-factor authentication (MFA), and unmanaged API tokens—but eliminating them at enterprise scale requires more than manual policy enforcement.
This is where Ankercloud’s achievement of the AWS Security Competency makes the difference. Backed by AWS’s rigorous validation, we provide enterprises with a proven, automated approach to securing identities, access, and workloads across complex environments.
Technical Pillars of Ankercloud’s AWS Security Competency
1. Automated Identity & Access Controls (CIEM + PAM)
- Continuous identity auditing powered by Cloud Infrastructure Entitlements Management (CIEM).
- Enforces least privilege by removing stale IAM users, deactivating unused access keys, and tightening role-based permissions.
- Integrated Privileged Access Management (PAM) to control, monitor, and rotate high-privilege credentials.
- Automated guardrails detect and remediate token sprawl, stopping unauthorized lateral movement.
2. Zero Trust and Continuous Verification
- Enforces Zero Trust Architecture across APIs, containers, and serverless functions.
- Real-time, context-aware access validation based on user identity, device posture, location, and workload sensitivity.
- Prevents privilege escalation, ransomware propagation, and insider threats through just-in-time (JIT) authorization.
3. AI-Powered Runtime Threat Detection
- Multi-source telemetry from AWS GuardDuty, AWS Security Hub, CloudTrail, and endpoint agents.
- Machine learning–driven anomaly detection and behavioural analytics to identify zero-day exploits, command-and-control traffic, and unusual API calls.
- Runtime security integration across Kubernetes, ECS, and Lambda functions to stop threats in real-time.
4. Compliance Automation for Regulatory Readiness
- Automated control mapping to GDPR, HIPAA, ISO 27001, and EU data protection standards.
- Continuous compliance monitoring and audit log ingestion into governance workflows.
- On-demand compliance reporting reduces manual audit overhead while ensuring continuous enforcement.
5. Unified & Scalable Security Operations (Cloud-Native SOC)
- Centralized telemetry ingestion across infrastructure-as-code, CI/CD pipelines, workloads, and SOC dashboards.
- Automated incident prioritization and response powered by AI-driven correlation.
- Mean-Time-To-Remediate (MTTR) reduced from weeks to minutes through playbook-driven workflows.
- 24/7 Managed Detection and Response (MDR) to scale protection across enterprise cloud environments.
Real-World Impact Across Industries
- Financial Services: Detected and prevented unauthorized IAM privilege escalation attempts, eliminating high-risk lateral movement paths across AWS and Azure environments.
- Healthcare: Automated HIPAA and GDPR compliance reporting integrated into the SOC, reducing security alert fatigue by 50% and streamlining audit readiness.
Why Choose Ankercloud
With cloud complexity increasing, security leaders can no longer rely on reactive, manual IAM policies. Enterprises require automated, scalable, validated solutions that close IAM gaps while reducing operational overhead.
Ankercloud’s AWS Security Competency demonstrates our technical excellence in:
- Eliminating IAM misconfigurations
- Enforcing Zero Trust policies
- Detecting advanced threats at runtime
- Automating compliance frameworks
- Scaling Security operations for cloud-native environments
By partnering with Ankercloud, enterprises gain a resilient IAM foundation that protects data, meets regulatory standards, and accelerates secure innovation.
From RBAC Chaos to PBAC Control: Data Governance on AWS
What if your data lake became a security labyrinth instead of a data goldmine? For too long, managing access to sensitive data in the cloud has felt like an endless game of patching permissions and untangling a web of static roles. Traditional access models like Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC) were the guardians of yesterday, but they are no match for the dynamic, multi-tenant needs of today’s large-scale data environments. In a world where compliance frameworks like GDPR and HIPAA are non-negotiable and data serves as a strategic product, these rigid methods often lead to over-permissioning, security vulnerabilities, and operational headaches.
That’s where Purpose-Based Access Control (PBAC) emerges not just as a better option, but as a strategic evolution in data governance. PBAC shifts the focus from static permissions to dynamic, context-aware access decisions driven by the specific purpose of the request. Instead of simply asking “Who are you?” or “What attributes do you have?”, PBAC also asks “Why do you need this data right now?”.
By incorporating the intended purpose into the decision-making process, PBAC delivers unmatched flexibility, security and compliance ensuring users get only the data necessary for their declared and approved purpose. This approach transforms your data lake from a potential liability into a governed, high-value business asset.
At Ankercloud, we take a research driven approach to implementing PBAC in modern cloud environments, leveraging AWS-native tools and custom policy logic to create secure, purpose-driven access frameworks that scale with your business.
Why Traditional Access Models Fall Short
The core of the problem with older models lies in their rigidity. RBAC, for example, assigns permissions based on static roles. As data environments grow, this can lead to a "role explosion," with dozens or even hundreds of roles to manage, making audits and updates a nightmare. ABAC introduced more flexibility by using attributes, but it too can become complex and unwieldy, requiring constant updates to maintain relevance.
These models struggle to keep pace with the modern reality of:
- Fine-Grained Access: The need for granular control over shared datasets at the column or cell level.
- Compliance Pressures: Strict frameworks like GDPR and HIPAA demand access controls that are provable and dynamically enforceable.
- Data as a Product: The shift to treating data as a product requires scalable, secure, and self-service access to accelerate innovation without compromising security.
PBAC offers a powerful alternative by decoupling access decisions from users, roles, or static attributes. Instead, it evaluates access based on centralized, dynamic policies, allowing for more flexibility, granularity, and maintainability.
A Research-Driven Approach: Implementing PBAC on AWS
Our team at Ankercloud recently explored how Purpose Based Access Control can be implemented in a modern AWS environment using native services. The goal was to evaluate how scalable and secure PBAC can be in real world data architectures. This research driven approach centers around three core AWS components that work in concert to create a robust and dynamic access control system:
- AWS Lake Formation LF-Tags: These tags are a powerful mechanism to define fine-grained access rules directly on your data assets. By applying tags like region=EU or department=Finance to specific tables, databases, or columns, you can create logical groupings that form the basis of your access policies.
- AWS Lambda: This is the brains of the operation. AWS Lambda serves as the dynamic policy engine, evaluating a user's context (e.g., their identity, the time of day, their device) against the LF-Tags of the requested data to make a real-time authorization decision.
- Amazon API Gateway: Acting as the secure entry point, API Gateway routes all data access requests to the Lambda function. This ensures that no data can be accessed without first passing through your centralized policy enforcement point, guaranteeing a single, auditable path for all data queries.
This architecture creates a seamless, secure, and scalable flow: a request comes in, API Gateway sends it to Lambda, Lambda checks the policy against the data's tags, and access is granted or denied all in real-time.
Top Use Cases & Real-World Impact
The power of PBAC truly shines in complex, distributed data environments. Consider a global retail company with departments like Marketing, Finance, and Supply Chain all accessing a shared enterprise data lake. The challenge is ensuring each department has restricted access based on region, role, or data type while meeting strict compliance standards.
- The Traditional Problem: Implementing this with RBAC would require creating dozens of static IAM roles and manually managing views for each department, leading to a high risk of over-permissioned access and administrative overhead.
- The PBAC Solution: With PBAC on AWS, data is tagged using LF-Tags (e.g., department=Marketing, region=EU, data_type=PII). An API Gateway handles incoming requests, and Lambda enforces policies in real-time. For example, a Marketing analyst from the EU requests customer data. PBAC automatically checks their access against the LF-Tags, and if the policy matches, access is granted otherwise, it is denied all without any manual intervention.
This approach is also critical for:
- Healthcare:
Ensuring doctors, researchers, and administrators only have access to specific patient data based on their role, location, or data sensitivity (e.g., genetic data vs. demographic data), aligning perfectly with HIPAA. - Financial Services:
Implementing granular controls for financial data, allowing analysts to view market trends without accessing sensitive customer account details, thereby meeting strict regulatory requirements. - Insurance Domain:
Enforcing purpose-driven access so claims adjusters can view only active claim files relevant to their region, underwriters can access risk assessment data without seeing personal health details, and fraud investigators can analyze flagged cases—supporting compliance with industry regulations and protecting customer privacy.
Basic idea of Implementation of PBAC Workflow in AWS

In AWS, Purpose Based Access Control (PBAC) uses dynamic, context-aware rules to decide who can access which data.
- User Request – A Marketing analyst, Finance officer, or Data analyst sends a query to the data lake through Amazon API Gateway.
- Purpose Evaluation – API Gateway forwards the request to an AWS Lambda purpose based engine, which checks:
- User context (identity, department, region, time, device)
- LF-Tags on the requested data (e.g., department=Finance, region=EU, data_type=PII) in AWS Lake Formation
- User context (identity, department, region, time, device)
- Decision – Lambda compares the user’s attributes to the LF-Tag policy:
- Match → Access granted
- No match → Access denied
- Match → Access granted
- Data Delivery – If approved, Lake Formation grants access to the dataset stored in Amazon S3 or queried via the Glue Data Catalog.
- Audit & Monitoring – Every decision is logged in CloudWatch and CloudTrail for compliance tracking (e.g., GDPR, HIPAA).
Example:
- A Marketing analyst in the EU requests customer purchase data. The Lambda engine checks that their department and region match the LF-Tags on the dataset. If tags match (department=Marketing, region=EU), they get access; if not, the request is denied—no manual intervention needed.
The Path to Modern Data Access: How Ankercloud Helps
Embracing PBAC is a strategic move, but its implementation requires deep expertise in modern cloud architecture, data governance, and security best practices. At Ankercloud, we don't just explore these solutions, we build them. We bring a proven, research-driven approach to help businesses transition from outdated access models to a dynamic and secure PBAC framework.
Our specialized services include:
- Strategic Consulting: We help you define your data governance and security objectives, translating them into a clear Purpose Based Access Control (PBAC) roadmap.
- Architecture & Implementation: We design and deploy the entire PBAC architecture on AWS, leveraging native services like Lake Formation, Lambda, and API Gateway for a scalable and secure solution.
- Custom Purpose Engine Development: We build and optimize your dynamic purpose evaluation engine, ensuring it's robust, efficient, and fully aligned with your business logic.
- Continuous Governance: We provide ongoing support to monitor, audit, and evolve your PBAC rules, ensuring your data remains secure and compliant as your business grows.
Our approach is rooted in continuous growth and learning. Big thanks to my team at Ankercloud for their dedication to exploring and building innovative solutions like this.
The future of business is autonomous, adaptive, and intelligent. Purpose Based Access Control ( PBAC) is the key to unlocking this potential securely. It is time to move beyond static, brittle access controls and empower your teams with safe, governed, and purpose-driven data access.
Ready to modernize your data access strategy?
Partner with Ankercloud to implement a cutting-edge PBAC solution that fortifies your data lake and accelerates your innovation. Contact us today.
FAQs
Some benefits of using cloud computing services include cost savings, scalability, flexibility, reliability, and increased collaboration.
Ankercloud takes data privacy and compliance seriously and adheres to industry best practices and standards to protect customer data. This includes implementing strong encryption, access controls, regular security audits, and compliance certifications such as ISO 27001, GDPR, and HIPAA, depending on the specific requirements of the customer. Learn More
The main types of cloud computing models are Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). Each offers different levels of control and management for users.
Public clouds are owned and operated by third-party providers, private clouds are dedicated to a single organization, and hybrid clouds combine elements of both public and private clouds. The choice depends on factors like security requirements, scalability needs, and budget constraints.
Cloud computing services typically offer pay-as-you-go or subscription-based pricing models, where users only pay for the resources they consume. Prices may vary based on factors like usage, storage, data transfer, and additional features.
The process of migrating applications to the cloud depends on various factors, including the complexity of the application, the chosen cloud provider, and the desired deployment model. It typically involves assessing your current environment, selecting the appropriate cloud services, planning the migration strategy, testing and validating the migration, and finally, executing the migration with minimal downtime.
Ankercloud provides various levels of support to its customers, including technical support, account management, training, and documentation. Customers can access support through various channels such as email, phone, chat, and a self-service knowledge base.
The Ankercloud Team loves to listen



.jpg)
.jpg)

.jpg)

.jpg)






-p-500.png)
.png)
.png)
.png)





.jpg)




.PNG)
