DevOps Pipeline and MLOps Pipeline Solutions

Ankercloud presents DevOps and MLOps Pipeline Solutions – a game-changing approach to streamlining your workflow, reducing bottlenecks, and achieving peak operational efficiency.
Our DevOps Pipeline Solutions empower your teams to automate and accelerate the software delivery lifecycle. From code commit to production deployment, we provide end-to-end solutions that enhance collaboration, increase agility, and ensure reliability.
Streamline Your Development with Ankercloud's DevOps Pipeline Solutions
We understands the criticality of efficient software development. Our DevOps Pipeline Solution is meticulously designed to automate and optimize every step of your development lifecycle. From code integration and testing to deployment and monitoring, our comprehensive solution ensures seamless collaboration among cross-functional teams. Benefit from shorter development cycles, reduced errors, and faster time-to-market, giving you a competitive edge.
Get full support from Ankercloud’s team to understand how these benefits apply to your specific business, and build a detailed cloud adoption plan before deciding to commit to the migration.
Continue reading


Mastering Machine Learning with Ankercloud’s MLOps Pipeline
Unlock the true potential of your machine learning projects with MLOps Pipeline Solution. Seamlessly manage, deploy, and monitor machine learning models at scale. Our solution bridges the gap between data science and operations, ensuring a smooth flow from model development to production deployment. Experience enhanced model accuracy, rapid iteration, and quicker insights, all while maintaining data integrity and security.
Continue reading
Check out case studies
Check out our blog
DevOps Trends: CI/CD Automation
CI/CD (Continuous Integration/Continuous Delivery) automation is a crucial aspect of DevOps practices and has been gaining significant attention in recent years. By automating the CI/CD pipeline, organizations can accelerate software delivery, improve code quality, and enhance collaboration between development and operations teams. Here are some notable trends in CI/CD automation:
- Shift-Left Testing: Shift-left testing emphasizes early and continuous testing throughout the software development lifecycle, starting from the earliest stages of development. By integrating testing into the CI/CD pipeline and automating the testing process, organizations can identify and address issues more quickly, reducing the risk of defects reaching production.
- Infrastructure as Code (IaC): Infrastructure as Code is a practice that enables the automation and management of infrastructure resources using code. With IaC, infrastructure configurations can be version-controlled, tested, and deployed alongside application code. CI/CD automation tools integrate with IaC frameworks such as Terraform or AWS CloudFormation to provision and manage infrastructure resources in a consistent and repeatable manner.
- Cloud-Native CI/CD: As organizations increasingly adopt cloud computing and containerization technologies, CI/CD pipelines are evolving to support cloud-native applications. Tools like Kubernetes and Docker are commonly used to build, deploy, and orchestrate containerized applications. CI/CD automation platforms are adapting to support the unique requirements of cloud-native environments, enabling seamless integration with container registries, orchestrators, and serverless platforms.
- Machine Learning/AI in CI/CD: Machine learning and AI techniques are being applied to CI/CD automation to optimize various aspects of the software delivery process. For example, AI-based algorithms can analyze code quality, identify patterns, and provide recommendations for improvements. Machine learning models can also be used to predict and detect anomalies in CI/CD pipelines, enabling proactive identification of potential issues.
- Low-Code/No-Code CI/CD: The rise of low-code/no-code development platforms has extended to CI/CD automation as well. These platforms provide visual interfaces and pre-built integrations that simplify the setup and configuration of CI/CD pipelines, reducing the need for extensive coding or scripting. Low-code/no-code CI/CD tools empower non-technical stakeholders to participate in the automation process and accelerate the delivery of applications.
Benefit of CI/CD: -
· Increased delivery speed & cooperation
· Instantaneous feedback
· Simple to maintain & Reliable
Components of a CI/CD Pipeline: -
a. Jenkins Pipeline: Jenkins Pipeline is a powerful and flexible way to define your continuous integration and continuous delivery (CI/CD) workflows in Jenkins. It allows you to define your build, test, and deployment stages as code, providing a consistent and repeatable process for your software development lifecycle. Jenkins Pipeline supports two syntaxes: Declarative Pipeline and Scripted Pipeline.
i. Declarative Pipeline: Declarative Pipeline provides a more structured and opinionated syntax for defining pipelines. It is recommended for most use cases as it offers simplicity and readability. Here’s an example of a simple Declarative Pipeline:
pipeline { agent any
stages { stage(‘Build’) { steps { // Perform the build steps here } }
stage(‘Test’) { steps { // Run your tests here } }
stage(‘Deploy’) { steps { // Deploy your application here }}}}
In this example, the pipeline has three stages: “Build,” “Test,” and “Deploy.” Each stage contains the necessary steps to be executed.
ii. Scripted Pipeline: Scripted Pipeline provides a more flexible and programmatic way to define your pipelines using Groovy scripting. It allows you to have greater control over the execution flow and provides more advanced features. Here’s an example of a simple Scripted Pipeline:
node {
stage(‘Build’) { // Perform the build steps here}
stage(‘Test’) { // Run your tests here }
stage(‘Deploy’) { // Deploy your application here }}
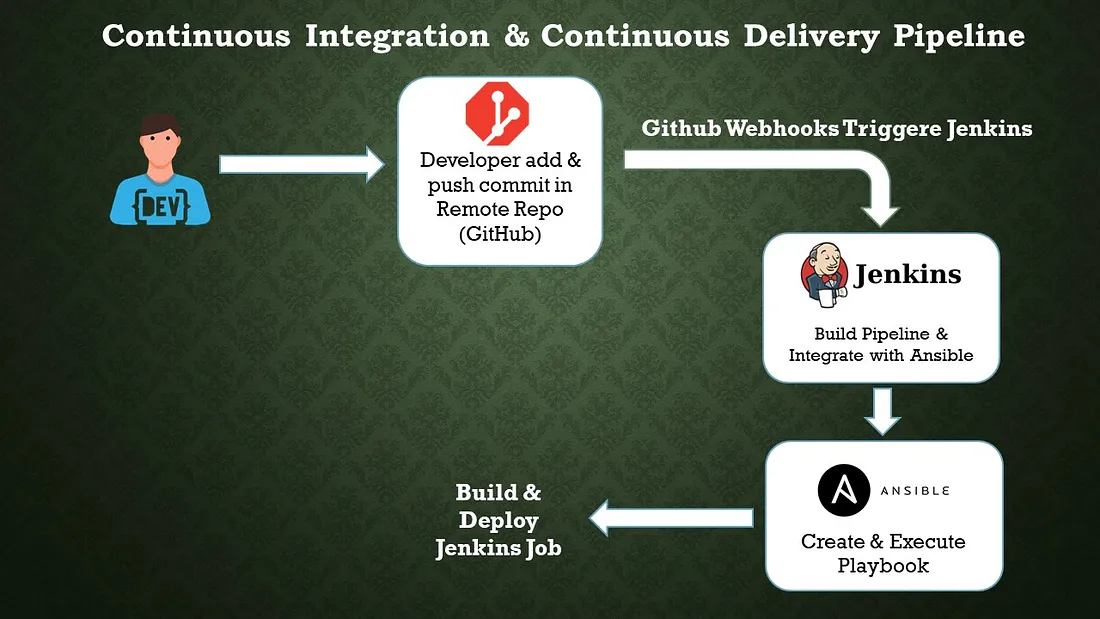
b. Configuration Management Tool: Ansible
Ansible is an open-source configuration management tool that automates the deployment, orchestration, and management of software applications and infrastructure. It is designed to be simple, agentless, and easy to use, making it popular among system administrators and DevOps teams. Here are some key features and concepts related to Ansible:
i. Agentless: Ansible does not require any agents or additional software to be installed on the target systems. It uses SSH (Secure Shell) and Python to communicate with remote hosts, which simplifies the setup process and reduces the overhead on managed systems.
ii. Declarative Language: Ansible uses a YAML-based language called Ansible Playbooks to define configurations and automate tasks. Playbooks are human-readable and describe the desired state of the systems. This declarative approach allows for idempotent execution, where running the same playbook multiple times produces consistent results.
iii. Inventory: Ansible uses an inventory file to define the hosts or systems it manages. The inventory can be a static file or generated dynamically from various sources, such as cloud providers or external scripts. It allows you to organize hosts into groups and apply different configurations to specific groups or individual hosts.
iv. Modules: Ansible comes with a wide range of built-in modules that perform specific tasks, such as managing packages, configuring services, manipulating files, or executing commands. Modules are written in Python and can be extended or customized to meet specific requirements.
v. Playbooks: Playbooks are the heart of Ansible. They are YAML files that define a set of tasks to be executed on remote hosts. Playbooks specify the desired state of the systems, and Ansible takes care of bringing them into that state. Playbooks can include variables, conditionals, loops, and handlers to perform complex configuration management.
vi. Idempotency: Ansible’s idempotent nature ensures that running the same playbook multiple times does not cause unintended changes. If a system is already in the desired state, Ansible skips the corresponding tasks, resulting in a consistent and reliable configuration management process.
vii. Ad-hoc Commands: Ansible allows you to execute ad-hoc commands directly on remote hosts without the need for writing a playbook. This feature is useful for quick troubleshooting, one-time tasks, or running simple commands across multiple systems simultaneously.
viii. Ansible Galaxy: Ansible Galaxy is a hub for sharing and discovering Ansible roles. Roles provide a way to organize and reuse playbook logic, making it easier to manage complex configurations. Ansible Galaxy allows you to find pre-built roles contributed by the community, helping you accelerate your automation efforts.
Conclusion:
Code quality is increased and changes are provided rapidly with CI/CD automation. The automation technique has a very good quality, bug-free, and quicker fault isolation impact. We completed every step of the automation process, including create, build, test, and deliver. Process automation is necessary for software development.
Streamline Your Development with Ankercloud's DevOps and MLOps Pipeline Solutions
In today's fast-paced technological landscape, staying ahead of the competition requires seamless integration, rapid deployment, and efficient management of development and machine learning operations. Ankercloud presents DevOps and MLOps Pipeline Solutions – a game-changing approach to streamlining your workflow, reducing bottlenecks, and achieving peak operational efficiency. In this article, we explore how Ankercloud's innovative pipeline solutions can revolutionize your development workflow.
Benefits of Ankerclouds DevOps and MLOps Pipeline Solutions
Enhanced Efficiency and Speed:
Ankercloud’s DevOps and MLOps Pipeline solutions are designed to accelerate your development lifecycle. With streamlined automation and continuous integration/continuous deployment (CI/CD) pipelines, your team can reduce manual interventions, leading to faster code deployment and quicker time-to-market for your applications and models.
Seamless Collaboration:
Collaboration is at the heart of successful development. Our Solution provides a collaborative platform where developers, testers, and data scientists can work together seamlessly. Shared pipelines, version control, and integration with popular project management tools foster a culture of teamwork, resulting in efficient problem-solving and improved software quality.
Reliable Testing and Quality Assurance:
We ensure that every code change and model update goes through rigorous testing and quality assurance processes. Automated testing environments, code reviews, and integration with testing frameworks guarantee that your software remains stable, secure, and bug-free.
Scalability and Flexibility:
As your projects grow, so do your infrastructure needs. Our solutions scale with your requirements, allowing you to handle larger workloads without compromising on performance. Whether you're managing a small application or a complex machine learning pipeline, Ankercloud solutions adapt to your needs.
Advanced Monitoring and Insights:
Gain deep insights into your development and deployment processes with comprehensive monitoring and analytics tools. We provide real-time performance metrics, logs, and reports, enabling you to make data-driven decisions to optimize your pipelines for maximum efficiency.
Secure and Compliant Practices:
Security and compliance are paramount in today's data-driven landscape. Ankercloud incorporates robust security features into its solutions, including access controls, encryption, and compliance with industry standards. Focus on your development while we take care of safeguarding your data and applications.
Simplified MLOps:
For teams working on machine learning projects, Ankerclouds' MLOps Pipeline solutions offer specialized features. From data preprocessing and model training to deployment and monitoring, We streamlines the end-to-end machine learning workflow, ensuring reproducibility and efficiency in your AI projects.
Conclusion:
Ankercloud's DevOps and MLOps Pipeline solutions offer a transformative approach to modern development practices. By automating key processes, fostering collaboration, and optimizing deployment, our pipelines empower your teams to focus on innovation and deliver high-quality software and machine learning solutions faster than ever before. Embrace the future of development with Ankercloud's cutting-edge pipeline solutions. Contact us today to learn how we can elevate your development workflow.
Understanding DevSecOps Concepts
DevSecOps, which stands for Development, Security, and Operations, is an approach that integrates security practices into the software development process. It emphasizes the collaboration and cooperation between development teams, security teams, and operations teams, with the goal of integrating security measures throughout the entire software development lifecycle.
There are several reasons why organizations adopt DevSecOps:
- Early Detection of Vulnerabilities: By incorporating security practices into the development process from the beginning, DevSecOps enables early detection and remediation of vulnerabilities. Security measures such as code analysis, vulnerability scanning, and penetration testing can be performed during development, reducing the chances of security issues going unnoticed until later stages.
- Rapid and Continuous Delivery: DevSecOps promotes the use of automation, continuous integration, and continuous delivery (CI/CD) pipelines. This approach enables faster and more frequent software releases while maintaining security standards. Security checks and tests can be automated and integrated into the CI/CD pipeline, ensuring that security is not compromised during the fast-paced development and deployment cycles.
- Collaboration and Shared Responsibility: DevSecOps emphasizes collaboration between development, security, and operations teams. It encourages breaking down silos and fostering a shared responsibility for security across different teams. This collaboration ensures that security considerations are not an afterthought but an integral part of the development process, leading to more secure and resilient software.
- Compliance and Regulatory Requirements: Many industries and organizations have stringent compliance and regulatory requirements concerning data protection and security. DevSecOps helps address these requirements by integrating security controls and practices into the development process. By automating security checks and documentation, organizations can demonstrate compliance more efficiently.
- Agile and Adaptive Security: DevSecOps aligns with the agile development methodology, allowing security practices to be implemented in an iterative and adaptive manner. Security measures can be continuously evaluated, improved, and adjusted based on changing threats and vulnerabilities. This enables organizations to respond more effectively to emerging security challenges.
- Enhanced Risk Management: Incorporating security into the development process allows organizations to identify and manage security risks more effectively. By addressing security concerns early on, the overall risk profile of the software can be reduced. DevSecOps provides visibility into potential risks and facilitates risk mitigation strategies.
Benefits of DevSecOps
DevSecOps, a combination of “Development,” “Security,” and “Operations,” is an approach that integrates security practices into the software development and deployment process. It emphasizes collaboration, automation, and continuous monitoring to ensure security measures are incorporated from the earliest stages of development. The benefits of DevSecOps include:
a. Early identification and mitigation of security vulnerabilities
b. Faster and more efficient software development
c. Improved collaboration and communication
d. Enhanced security awareness and culture
e. Automated security testing and monitoring
f. Continuous compliance and auditing
g. Rapid incident response and recovery
h. Cost-effectiveness
Types of Security Techniques
In DevSecOps (Development, Security, and Operations), security techniques are integrated into the entire software development lifecycle to ensure the continuous delivery of secure and reliable software. Here are some common security techniques used in DevSecOps:
i. Static Application Security Testing (SAST): SAST involves analyzing the application’s source code or binary without executing it. It helps identify security vulnerabilities, such as insecure coding practices, potential backdoors, or known vulnerabilities in third-party libraries.
ii. Dynamic Application Security Testing (DAST): DAST involves testing an application in a running state to identify vulnerabilities. It simulates attacks on the application to find security weaknesses, such as injection flaws, cross-site scripting (XSS), or improper access controls.
iii. Interactive Application Security Testing (IAST): IAST combines elements of both SAST and DAST. It instruments the application during runtime to monitor its behavior and identify vulnerabilities. It provides more accurate results by analyzing code execution paths.
iv. Security Code Reviews: Manual code reviews are performed by security experts to identify security flaws that might be missed by automated tools. This technique involves a thorough examination of the codebase, looking for vulnerabilities or insecure coding practices.
v. Security Testing Automation: Automation tools can be used to perform various security tests, including vulnerability scanning, penetration testing, and security assessment. These tools help identify common vulnerabilities efficiently and enable continuous security testing.
vi. Container Security: When using containerization technologies like Docker or Kubernetes, container security techniques are essential. This includes scanning container images for vulnerabilities, enforcing secure container configurations, and monitoring container runtime behavior.
vii. Infrastructure as Code (IaC) Security: DevSecOps also focuses on securing the infrastructure by applying security practices to infrastructure-as-code (IaC) templates. This involves implementing secure configurations, scanning IaC templates for security vulnerabilities, and performing automated security checks during infrastructure deployment.
Advantages of DevSecOps:
1. Recognize Bugs and Vulnerabilities Early.
2. Use open source with assurance.
3. Reduce resource management costs.
4. Educate developers about security.
5. Minimize Legal Liability and Risk
Conclusion:
DevSecOps promotes a proactive approach to security by integrating it into the software development lifecycle. It enables early detection of vulnerabilities, facilitates faster and more frequent releases, fosters collaboration and shared responsibility, ensures compliance with regulations, supports agile and adaptive security practices, and enhances overall risk management.
The Ankercloud Team loves to listen










.png)







.jpg)