Email Spoofing: What is it and How to Protect Against it

E-mail spoofing is a technique whereby the attacker forges the sender's address in such a way as to make the recipient believe it is coming from a trusted party. It could be a colleague in the office, a company, or even a financial institution. In this scenario, an attacker sends email headers in a manner such that the recipient would consider it to have come from a particular person, and the possibility of getting people to click on links they should not download attachments that will harm them or share with sensitive information becomes more probable.
Most of the current email systems lack a good feature that identifies forged sender addresses, and this explains why most phishing, spear-phishing, and business email compromise attacks rely on such a strategy.
For example, you might get an email that you are in both "To" and "From." Now, that doesn't mean someone has breached your email account. What they would do instead is pretend to be you or maybe another person you trust so that you open the email and may click on malicious links or release sensitive information.
How to Identify a Spoofed Email?
Sent Folder does not have an e-mail - When you send yourself an e-mail, it always is going to be in your Sent folder. And consequently, since spammers spoofed your address, you'd never see it there because he sent it from nowhere, but it would appear as if it was from your account.
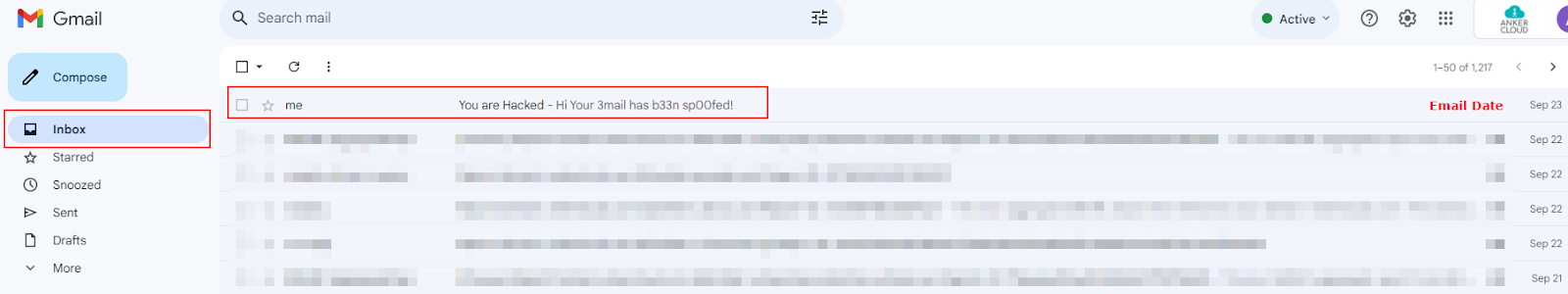
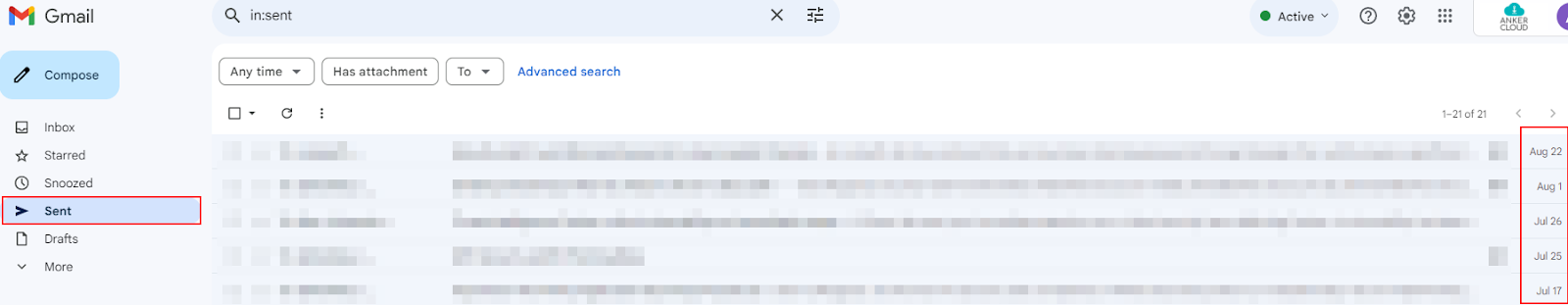
NOTE: If you compose an email to yourself and delete it from your sent folder, then you will no longer see the email in your inbox also.
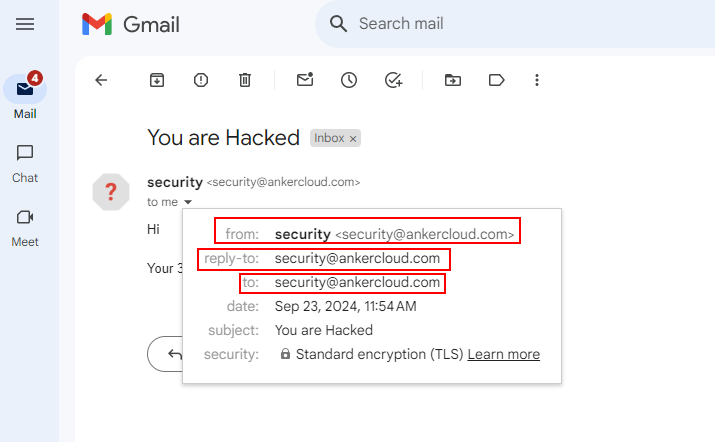
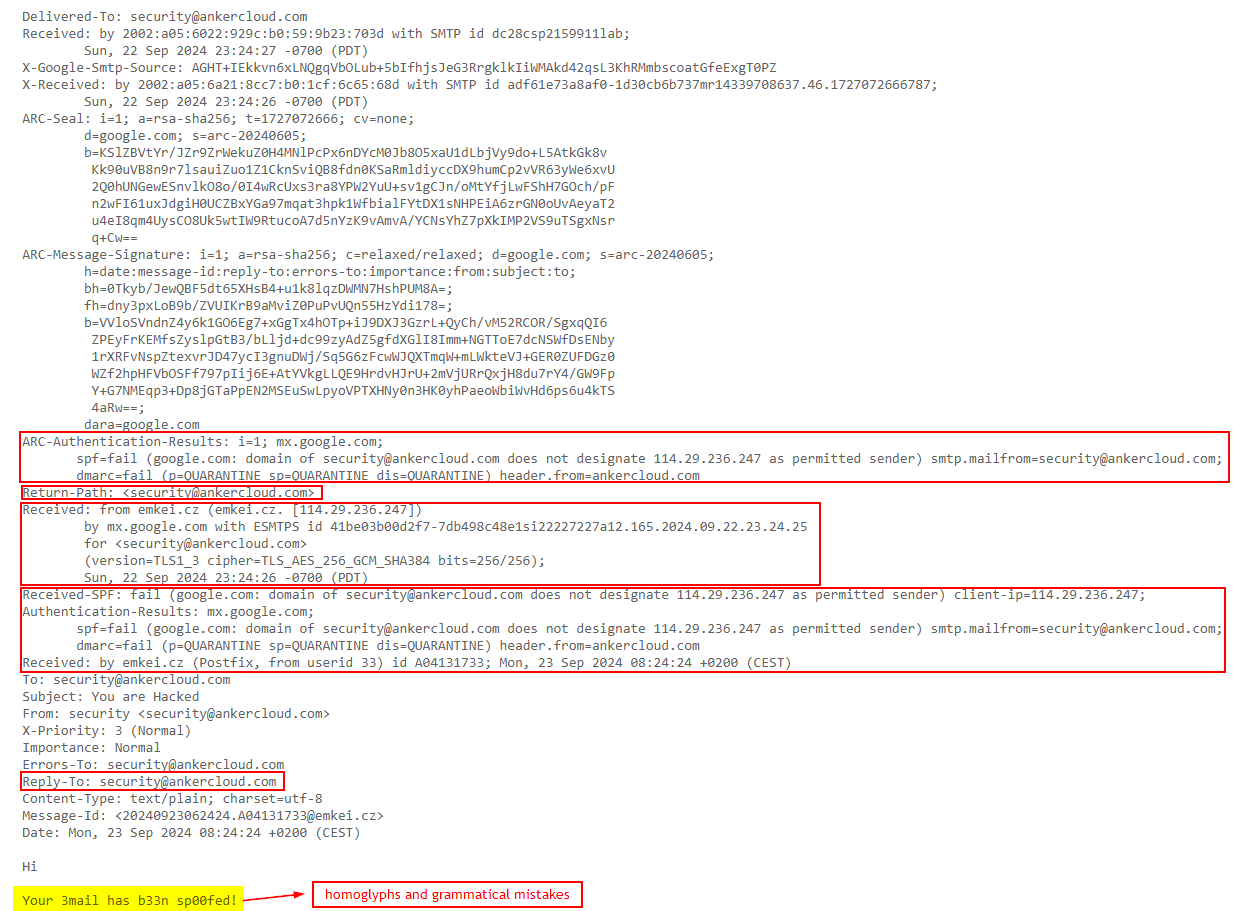
Check the Original Email - Most E-mail systems will show you the "original" or "raw" version of an e-mail. This shows all the technical details of how the e-mail is sent. Look for a possible sign such as suspicious From, Reply-To, Return-Path, or Received, fields that don't look just right, maybe an indicator of a spoofed e-mail.
Grammar and spelling mistakes - Always keep an eye out for homoglyphs (Example: Ankercloud as Amk3rc10ud) and grammatical errors that a legitimate sender would never make.

Preventive measures: protecting both yourself and your organization
- Implement the SPF, DKIM, and DMARC email security protocols as a layer of protection against spoofing which helps in verifying that an email was actually sent from the person that it says it is, if not then the email will go to spam/deleted immediately.
- Use spam filters- Generally, most email services have spam filters. These can filter suspicious-looking emails even before they reach your inbox. To be on the safe side, assume that your spam filter is active.
- Be Cautious - Be wary of opening any uncalled-for emails, particularly when suspicious, or asking for information that could be confidential.
What to Do If You Fall Victim to Spoofing Attack
- Don’t panic and disconnect the device from the internet immediately, to make sure no further damage is done by the malicious programs downloaded.
- Report the IT team on what happened so they can decide if sensitive information has been put at risk and make all the necessary arrangements to ensure safety measures are taken about your account.
- Change your passwords in case you think you got infected, change all the passwords right away from a different device, and implement/enforce 2FA for that added layer of security.
- Keep an eye on your email account and other accounts online for suspicious activities such as unauthorized login attempts or suspicious activities through your accounts.
Conclusion
Email spoofing is very hard to prevent, but definitely difficult to detect; if you are alert and think of some basic precautions, you should never fall for such a scam. So, always check suspicious emails and contact your IT/security team whenever in doubt, please ask for help.
Related Blogs
Build Trust, Secure Deals: Ankercloud's Approach to Compliance and Trust Management
The Imperative of Trust in Modern Business
In a world where nearly 60% of corporate data resides within cloud storage systems, establishing and maintaining trust is critical. The surge in cloud adoption stems from its unparalleled speed, agility, and flexibility, enabling businesses to innovate and deliver cutting-edge products and services. However, this rapid migration to the cloud introduces inherent security risks.
The complexity and expansive nature of cloud infrastructures create a larger attack surface, potentially exposing sensitive data to cyber threats. To counter these risks, adherence to stringent compliance frameworks is essential. These frameworks encompass a range of regulatory requirements and industry-specific standards, acting as a shield against vulnerabilities.
Ankercloud's Approach: Security Assessments and Trust Management
We have crafted a holistic approach to compliance and trust management that empowers businesses to navigate the complexities of the digital landscape and secure their future. Here's how we do it:
Rigorous Security Assessments
Ankercloud's proactive stance on security involves regular, comprehensive security assessments. These evaluations cover every aspect of the infrastructure, from physical security to data encryption and access controls. Regular penetration testing and vulnerability assessments ensure that potential weaknesses are identified and fortified. This meticulous approach not only protects our systems but also instills confidence in clients regarding the safety and privacy of their data.
Compliance Simplified
We specialize in simplifying compliance audits, ensuring that the process is not a burden on your engineering and security teams. Ankercloud expedites the implementation of essential compliance frameworks, including SOC 2, ISO 27001, HIPAA, GDPR, USDP, and custom frameworks, in weeks, not months. Our approach, certified through trusted platforms like Vanta, enhances and validates your security posture.
Trust Enhancement through Integrated Security Measures
In the cybersecurity domain, identity-based attacks constitute a significant percentage of threats. Ankercloud integrates with advanced solutions like Unosecur to fortify cloud infrastructure against identity threats. Unosecur offers real-time identity visibility, continuous user profiling, and proactive identification of risks, promoting swift remediation with automated workflows. This integration not only enhances security but also fosters collaboration between security and DevOps teams for an agile response to threats.
Data Encryption:
Data security is a top priority for Ankercloud. All data at rest and in transit is encrypted using state-of-the-art encryption algorithms. This robust encryption ensures that even if a breach were to occur, the data would remain unintelligible to unauthorized individuals.
Disaster Recovery and Redundancy:
Ankercloud's infrastructure is designed to ensure business continuity. Redundant data centers and disaster recovery plans guarantee that even in the event of a catastrophic failure, data remains accessible and secure.
Flexibility and Customization:
Ankercloud recognizes that different businesses have unique security and compliance requirements. As a result, We offer flexible solutions that can be tailored to the specific needs of each client, demonstrating our commitment to understanding and meeting customer expectations.
Transparent Communication
Open communication is key to building and maintaining trust. Ankercloud prioritizes transparent communication with its clients, keeping them informed about any system updates, potential risks, and the actions taken to mitigate them. Regular reports and dashboards offer clients a clear view of their data's security status, fostering a sense of collaboration and trust.
Client-Centric Approach
Ankercloud's commitment to trust management is evident in its client-centric approach. We offer a transparent and personalized service that includes regular reporting on security and compliance status. This transparency fosters trust by keeping clients informed about the steps taken to protect their data.
Moreover, Our customer support is responsive and readily available to address any concerns or inquiries. Clients appreciate the open line of communication, which further strengthens the trust between Ankercloud and its partners.
Trust Management Strategies for Sustainable Partnerships
Ankercloud's trust management strategies extend beyond mere compliance. The company appreciates that fostering trust is an ongoing process. Through transparent communication, ethical practices, and a commitment to maintaining the highest standards, Ankercloud ensures that partners and clients feel assured and valued at every step of their engagement.
The provision of clear and concise policies, coupled with regular updates and educational resources, empowers partners to comprehend and actively participate in the shared responsibility of trust and security. Ankercloud’s emphasis on collaboration and transparency sets the stage for building enduring partnerships based on mutual respect and reliability.
Building Trust for Growth and Success
In a world where trust can make or break a business, Ankercloud's approach to compliance and trust management is a game-changer. By ensuring robust security, simplifying compliance, and leveraging trust as a competitive advantage, we help businesses establish and maintain trust with partners, customers, and investors. Trust is not just an intangible asset; it's a catalyst for growth and success.
Businesses that prioritize trust are better positioned to thrive in today's digital landscape. Ankercloud is your trusted partner in this journey. Contact us today to explore how our services can fortify your security, streamline compliance, and elevate trust to new heights, giving your business the competitive edge it deserves. Build trust, secure deals, and seize opportunities for growth and success with Ankercloud by your side.
Cloud Compliance and Data Protection Services: Ensuring a Secure Cloud Environment with Ankercloud
In a data-centric world, the protection of sensitive information and adherence to regulatory requirements have grown into crucial priorities for businesses, regardless of their scale. Recent years have seen a notable surge in cybersecurity threats, coupled with the introduction of multiple legislations aimed at safeguarding data and privacy. These regulations, such as GDPR, HIPAA, ISO/IEC 27001, and PCI DSS, place rigorous expectations on how data is handled and secured within organizations. Non-compliance with these regulations can result in substantial financial penalties, legal consequences, and harm to an organization's standing.
In this article, we will delve into the evolving landscape of data protection and regulatory compliance, exploring the essential measures and strategies that businesses must adopt to navigate this complex terrain successfully.
The Importance of Cloud Compliance and Data Protection
As the volume of data processed and stored in the cloud continues to soar, the need for robust data protection and compliance measures becomes more critical than ever. Various factors underscore the significance of this:
1. Data Privacy Regulations
Laws such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) impose strict requirements on the handling of personal and sensitive data. Non-compliance can result in hefty fines.
2. Cybersecurity Threats
The digital realm is rife with threats, from data breaches to ransomware attacks. Effective data protection is a fundamental defense against these risks.
3. Customer Trust
Building trust with your clients is paramount. Demonstrating that their data is secure and compliant with relevant regulations is a significant factor in gaining and maintaining their trust.
4. Business Continuity
Data loss or breaches can have devastating consequences for your business, including operational disruptions, financial losses, and damage to your reputation. Proper data protection and backup strategies are essential for business continuity.
Cloud Compliance and Data Protection with Ankercloud
While AWS goes to great lengths to ensure compliance with industry standards and legal requirements, it's crucial for customers to implement preventive measures and maintain the confidentiality, availability, and integrity of their data. Ankercloud, an AWS advanced partner, offers guidance and technical support to help businesses achieve and maintain compliance.
Our Comprehensive Services Include
1. Security Strategy Analysis
We begin by analyzing your existing cloud environment, helping you identify areas where improvements are needed. This analysis sets the stage for creating a tailored security strategy that aligns with your unique requirements.
2. Centralized Policies for User Control
We assist you in developing centralized policies that give you full control over your users' actions. This ensures that your cloud environment operates in compliance with the strictest security standards.
3. IAM User Management
Our experts provide the necessary tools and guidance for efficient Identity and Access Management (IAM) user management. This critical component ensures that access is restricted to authorized individuals only.
4. Defensive Controls
We help you implement robust defensive controls to protect your AWS infrastructure. From firewalls to intrusion detection systems, our team ensures that your cloud environment is well-protected against external threats.
5. In-Depth Infrastructure Reviews
Our team conducts thorough reviews of your AWS infrastructure to identify vulnerabilities and areas for improvement. We leave no stone unturned in the quest for cloud security.
6. Cloud Workload Design and Maintenance
Designing and maintaining new cloud workloads in line with best practices is one of our key strengths. We ensure that your cloud architecture is not only secure but also optimized for performance.
7. Ongoing Support
Cloud compliance is not a one-time task but an ongoing commitment. We provide continuous support for secure infrastructure management, monitoring, and uptime, ensuring that your cloud environment remains resilient.
In the world of cloud computing, waiting to address security concerns after an incident occurs can be highly ineffective and lead to irreversible losses. The consequences could include data breaches, service downtime, financial losses, and customer dissatisfaction. Ankercloud emphasizes the importance of taking proactive steps to ensure that your AWS environment is secure, compliant, and resilient.
So, if you want to ensure that your cloud infrastructure is secure, compliant, and ready to face any challenge, don't wait—take action now with Ankercloud. Our expertise, combined with the robust security features of AWS, is your recipe for success in the ever-evolving cloud landscape.
ISO 27001:2022 Made Easy: How Ankercloud and Vanta Simplify Compliance
At Ankercloud, our commitment to information security is reflected in our ISO 27001:2022 certification. Leveraging our expertise and advanced tools, we help other organizations achieve the same certification efficiently. With Vanta, we ensure a streamlined, automated, and effective compliance journey, showcasing our dedication to the highest standards of information security.
What is ISO 27001:2022?
ISO 27001:2022 is a global standard for managing and protecting sensitive company information through an Information Security Management System (ISMS). It ensures the confidentiality, integrity, and availability of data by providing a structured approach to managing information security risks.
The ISO 27001:2022 Process (Traditional Approach)
Obtaining ISO 27001 certification requires the following crucial steps
Preparation (1-3 months)
Familiarize with the standard, define the scope, and Perform an initial gap analysis
Implementation (3-6 months)
Develop an ISMS, conduct risk assessments, Implement necessary controls, and document policies
Internal Audit (1-2 months)
Evaluate compliance with the ISMS and identify improvements
Management Review (1 month)
Review ISMS performance and align with organizational objectives
Certification Audit (1-2 months)
Engage a certification body for stage 1 (document review) and stage 2 (on-site assessment) audits
Post-Certification (Ongoing)
Continuously monitor, conduct internal audits, and perform management reviews
In total, the process can take about 6 to 12 months, depending on factors like the organization's size, complexity, and preparedness.
How Vanta Simplifies ISO 27001:2022 Compliance
Vanta, a compliance automation platform, transforms the compliance process by automating security monitoring and evidence collection, making ISO 27001:2022 compliance more manageable. Here's how:
- Automated Security Monitoring: Vanta continuously monitors your systems for security issues, ensuring you meet ISO 27001:2022 requirements without manual intervention.
- Evidence Collection: Vanta automates 90% of the evidence collection, such as access logs, security configurations, and compliance status reports.
- Compliance Management: A centralized dashboard helps manage and track compliance efforts, simplifying the process.
- Risk Assessment: Vanta identifies vulnerabilities and risks, providing effective recommendations.
- Automated Documentation: Generates and maintains required documentation for audits, reducing the manual workload.
With Vanta's automation approach, the ISO 27001:2022 certification process can be significantly expedited, allowing organizations to achieve certification in as little as 2 to 3 months. This accelerated timeline is made possible by Vanta's efficient, automated workflows and continuous monitoring, which streamline compliance tasks and reduce the time typically required for manual processes.
Benefits of Using Vanta Compliance Tools Compared to Traditional Methods
Vanta offers numerous advantages over traditional compliance methods:
- Simplified Management and Guidance: Reduces complexities and provides step-by-step guidance, lowering the administrative burden.
- Automated Detection and Proactive Assessment: Ensures timely identification and prioritization of security risks.
- Real-time Dashboards and Streamlined Audits: Provides immediate visibility into compliance status and simplifies audit preparation.
- Seamless Integration and User-Friendly Interface: Enhances workflow efficiency with seamless integration and an intuitive interface.
- Enhanced Data Protection and Trust Building: Strengthens data protection and demonstrates strong security practices to stakeholders.
- Time and Cost Savings with Continuous Monitoring: Automation reduces time and costs, while continuous monitoring ensures long-term security and compliance.
How Ankercloud Can Help Companies Achieve ISO 27001:2022 Certification Using Vanta
As ISO 27001:2022 certified lead auditors, Ankercloud enhances organizations' information security practices, ensuring compliance with legal and regulatory requirements. We equip organizations with the skills to effectively manage risks, fostering a proactive approach to data protection. Implementing ISO 27001:2022 can streamline operations, improve efficiency, and build trust with customers and stakeholders.
- Expert Guidance: Ankercloud's expertise guides companies through the ISO 27001:2022 process efficiently.
- Platform Utilization: Vanta's automation and monitoring tools streamline compliance.
- Customized Support: Tailored services meet specific company needs, ensuring comprehensive ISO 27001:2022 coverage.
- Accelerated Timeline: Vanta's automated processes and Ankercloud's expertise enable faster ISO certification.
- Continuous Improvement: Ankercloud helps maintain and improve ISMS post-certification, ensuring ongoing compliance and security.
Conclusion
Ankercloud's expertise, combined with Vanta's automation capabilities, offers a powerful solution for companies seeking ISO 27001:2022 certification. By streamlining the compliance process through automated security monitoring, evidence collection, and compliance management, Ankercloud helps companies achieve certification efficiently and effectively. Leveraging Vanta, Ankercloud ensures a smooth and cost-effective journey to certification, enhancing the overall security posture of your organization.


